Encryption tools for business data play a vital role in safeguarding sensitive information from unauthorized access. In an era where data breaches are increasingly common, understanding the significance of encryption is essential for every organization. By implementing robust encryption methods, businesses can not only protect their vital assets but also ensure compliance with various data protection regulations, thereby mitigating risks associated with unencrypted data.
With various types of encryption tools available, it becomes crucial for businesses to choose the right methods that suit their specific needs. From symmetric to asymmetric encryption, the landscape is diverse, and knowing the tools at your disposal can empower organizations to enhance their data security significantly. As we delve deeper, we’ll explore how to effectively implement these tools, evaluate their performance, and stay ahead of future trends in encryption technology.
Importance of Encryption for Business Data
In today’s digital landscape, the protection of sensitive business information is paramount. Encryption plays a crucial role in safeguarding this data from unauthorized access and breaches. As businesses increasingly rely on digital platforms, the need for robust encryption methods has never been more significant.
Unencrypted data poses severe risks, including data breaches that can lead to financial loss, damage to reputation, and legal implications. Cybercriminals often target unprotected information, exploiting vulnerabilities to access sensitive customer data, trade secrets, or financial records. Furthermore, encryption not only serves as a defense mechanism but also aids organizations in complying with data protection regulations such as GDPR and HIPAA, ensuring that they meet legal requirements for handling sensitive information.
Types of Encryption Tools Available
Understanding the different types of encryption methods available is essential for selecting the right tools for business needs. There are primarily two categories of encryption: symmetric and asymmetric encryption.
- Symmetric Encryption: This method uses a single key for both encryption and decryption, making it faster but requiring secure key management. Examples include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
- Asymmetric Encryption: Utilizing a pair of keys (public and private), this method enhances security but is generally slower. An example is RSA (Rivest-Shamir-Adleman) encryption.
Popular encryption tools widely adopted by businesses include:
– VeraCrypt
– BitLocker
– OpenSSL
– AxCrypt
The choice of encryption software often depends on the specific requirements of the organization, including the level of security needed, ease of use, and integration capabilities with existing systems.
Implementing Encryption Tools
Successfully implementing encryption tools within a business involves several critical steps:
- Assess the data that needs protection and identify sensitive information.
- Choose the appropriate encryption method based on the organization’s needs.
- Deploy encryption tools across all relevant platforms and devices.
- Train employees on how to use encryption tools effectively.
- Regularly review and update encryption practices to adapt to new threats.
Best practices for selecting encryption tools include evaluating scalability, compatibility with existing infrastructure, and user-friendliness. Common pitfalls to avoid include inadequate key management, neglecting to encrypt all sensitive data, and failing to provide adequate training for employees on encryption practices.
Evaluating the Effectiveness of Encryption Tools, Encryption tools for business data
To ensure encryption tools are effectively protecting data, businesses can utilize various metrics, such as:
– Frequency of data breaches post-encryption.
– User feedback on tool usability.
– Performance impact on systems.
Successful case studies, such as organizations that achieved zero data breaches after implementing robust encryption protocols, provide compelling evidence of encryption effectiveness. Comparisons between different encryption tools can also reveal significant differences in performance, security level, and usability, guiding businesses in making informed choices.
Future Trends in Encryption Technology
Emerging trends in encryption technologies are shaping the future of data security in businesses. Quantum encryption, for instance, promises unparalleled security through principles of quantum mechanics, making it nearly impossible for hackers to intercept data without detection.
As cyber threats evolve, encryption will also need to adapt. Predictions for the future include the increased adoption of artificial intelligence in managing encryption processes, enhancing real-time protection against data breaches and other cyber threats.
Training and Awareness on Encryption Practices
Creating a comprehensive training program for employees is vital to promote the importance of encryption in protecting business data. This program should include:
– Interactive workshops on encryption tools and their applications.
– Regular updates on emerging threats and security practices.
Methods to raise awareness across the organization could involve informative newsletters, dedicated intranet resources, and engaging presentations by cybersecurity experts. Providing a curated list of resources for employees to learn more about encryption and data security, such as online courses, webinars, and articles, can further enhance their understanding and commitment to data protection.
Legal and Ethical Considerations in Encryption
The legal implications of data encryption vary across industries, with some sectors like healthcare and finance facing stricter regulations. Organizations must navigate these legal landscapes carefully to avoid penalties and comply with laws regarding data protection.
Ethical responsibilities associated with handling encrypted data include ensuring the security of customer information and maintaining transparency about how data is protected. This commitment to ethical practices can significantly affect customer trust and, ultimately, corporate reputation in the marketplace.
Conclusive Thoughts: Encryption Tools For Business Data
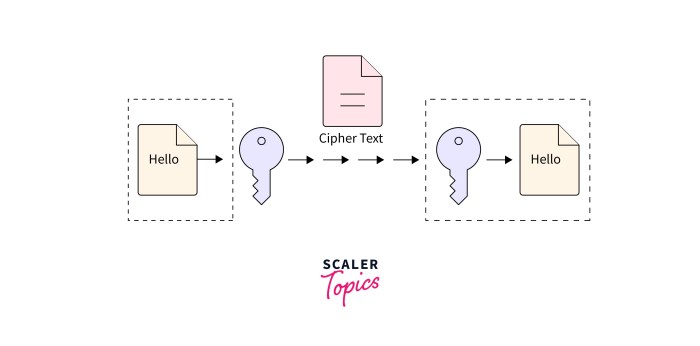
In conclusion, the discussion on encryption tools for business data highlights the imperative nature of protecting sensitive information in today’s digital landscape. By understanding the types of tools available, implementing them effectively, and fostering a culture of awareness and compliance, businesses can navigate the complexities of data security with confidence. As encryption technology continues to evolve, staying informed about emerging trends will be vital in safeguarding business data against ever-evolving cyber threats.